Executive Online Risk Management
How To Protect Your Private Data and Mitigate the Risk of Fraud?
In today’s digital society, it has never been more important to mitigate the risk of having sensitive, private data available to the public. Sensitive data that is misused by criminals can result in spoofing attempts, fraud, or even personal threats. Such as executive impersonations.
To mitigate such risks, Thomsen Trampedach has developed a service that aims to present the individual with a digital footprint report in which potential risks to the individual and their close family members are mapped out.
Aside from identifying potentially sensitive data, the service also aims to identify any false statements harming the reputation of the individual, or content that is objectionable/sensitive and should therefore not be accessible to the public.
Thomsen Trampedach will identify and score the most relevant cases of abuse/objectionable content and provide recommendations on possible responses in a timely manner that would remove or reduce the risk.
Our Solution
Our solution involves a digital footprint report with an overview for the purpose of pointing out the data that has a risk attached to it. Every case (URL) will be presented together with a recommendation on how to deal with the unwanted content. Upon receiving the first footprint report, the individual can decide on frequency at which on-going monitoring should be conducted. Every case will be presented in our web-based case management system Pliano.
Detection
Monitoring Main Social Networks (Facebook.com, VK.com, Twitter.com, Youtube.com, Reddit.com, Instagram.com, Wechat.com, and Linkedin.com)
Monitoring of Main Search Engines (Google, Yandex, Baidu)
Proactive Identification of data prone to misuse, such as: 1) addresses; 2) dates of birth; 3) names and other detail relating to family members; 4) information related to the background of the individual (place of birth etc.); 5) signatures; 6) social security numbers and other official identifiers; 7) false and / or objectionable content.
Investigation & Enforcement
For all relevant cases identified, Thomsen Trampedach will provide a recommendation as to how to approach removing the profiles or personal data in question or mitigating its impact where removal is not possible. An overview of the cases will be available at any moment in Pliano. In Pliano, once a case has been added, the client will get notified.

We store all relevant data related to the case in Pliano®. Each “case” includes a URL, investigation notes, suggested action, a screenshot, the takedown process and correspondence.
Premade enforcement mechanisms for over 200 + Marketplaces.
Your Questions
Our Answers
We begin with checking main Social Networks (Facebook.com, VK.com; Instagram.com, Wechat.com, Linkedin.com):
- Conducting name-based searches on Facebook.com utilizing the full name of the Report Subject.
- Investigating the presence of his/her relatives on the platforms and look for “open profiles” in order to collect further information.
- Analyzing all the available pictures including the “likes” and the “comments” received under the pictures of the Report Subject or the already identified close relatives’ profiles.
- Analyzing posts, comments, and the provided personal information, including the “groups”, “places”, and “pages he/she likes” sections.
- Conducting the same extensive search for all the relevant social media platforms.
- Utilizing specifically dedicated software to gather and connect further information (with particular attention to the post the Report Subject liked on the platforms when such information would be available).
We continue with checking main Internet search engines results (Google, Yandex, Baidu):
- Conducting extensive name-based queries.
- Conducting image searches utilizing the Report Subject social media profile pictures.
- Conducting search engines queries utilizing all other relevant identifiers (i.e. phone number, company name, close relatives’ names).
- Conducting the searches by changing the IP address to the relevant geographical area for the specific case.
In addition, we, conduct Reverse WHOIS searches:
- Utilizing the Report Subject’s name and/or email
- Utilizing the Report Subject’s family members names and/or emails
- Conducting WHOIS searches for all the website connected to the Report Subjects and/or his/her relatives
Finally, we produce a report that is sent monthly or after preferred periodically.
- Reporting the content in a clear and exhaustive form, comprehensive of links to content representing a digital risk to the Report Subject and exemplifying screenshots.
- Providing a risk evaluation for each case, taking into consideration the overall results and their interconnection.
- Providing tailored recommendations for resolving or mitigate the identified digital risks.
We also help to remove unwanted content that has been identified through this service on an ad-hoc basis.
- When registering your account, do not provide sensitive personal information where this is not absolutely necessary. Sensitive personal information includes, among others, your social security number, passport number, physical address, phone number, date of birth, bank account information or your family members’ personal information. This information can easily be used for impersonation or socially engineered scams.
- Check your privacy settings (and that of your relatives as well), and exercise control and foresight over what you post and to who this is available. Official links to six social media platforms with examples on how to control privacy settings can be found below:
Facebook Twitter Instagram LinkedIn VKontakte Weibo
- Check app permissions carefully. Permissions granted to various app can allow these to gather information about your exact location, as well as information related to your email account, on the basis of their Terms and Conditions. Some apps may also gather information unrelated to the usage of the app, accessing your personal information from messages and storing one – time passwords.
- Close the accounts that you’re not using. There is a high risk that old social media accounts will be compromised due to weak passwords used in the past, or due to weak two factor authentication with questions that can easily be answered by strangers, e.g. “What is the name of your pet?”.
- Delete third-party account connections: It is not necessarily wrong to have your Facebook or Twitter accounts connected to other apps, but you should keep these connections to a minimum and remove the ones that you are not using. For example, if you use Facebook to sign-up for an app, you may grant this app read-write access to potentially sensitive information on your Facebook profile. Visit the following section (link) of the Facebook help center to find out how to minimize the Facebook permissions granted to apps
- Install a VPN (Virtual Private Network). By installing a VPN on your devices you can spoof your location and add an extra layer of security to the data you are sending and receiving; allowing you to stay anonymous while surfing online. Without a VPN your IP address may reveal the city, zip code and area corresponding to your address. To learn more about your IP address and the information it leaves behind, you can visit the following website (link). Visit (link) find a selection of different VPN providers.
- Take advantage of search engine’s built-in filters. Many search engines give you the option of choosing a “safer” search when using their services. For example, you can check this link to see how to use SafeSearch on Google, and the following on the safe search plug-in for Firefox.
- Check security when shopping online. Verify security symbols and encryptions before entering any credit or identification details. Make sure the URL (the website address) seems legitimate (i.e. that the domain name hasn’t change when proceeding to order), and that it is encrypted behind a SSL certificate. A SSL certificate secures your connection to the website by encrypting any sensitive information that you provide, such as credit card information, usernames, passwords etc. An easy way to know if the website is SSL certified, is to evaluate the websites URL, and check whether the connection type is (“http” or “https”), if the connection type is “https”, the website is normally secure behind a SSL certificate. For additional information on how to find out if a website is legitimate please visit the following (link).
- Turn on automatic updates for security software. Software companies provide free updates to fix security issues and other problems related to the software in question.
- Make sure that you download content and applications only from official sources, such as official app stores. Illicit apps or downloads may abuse your personal data. Therefore, before downloading any app, check out online reviews, and always be careful with providing your payment details.
Step 1
Privacy Checkup
First step and the easiest one for checking your Facebook privacy settings is to perform a Privacy Checkup.
Click on the question mark symbol in the top right of the Facebook page and select Privacy Check-up
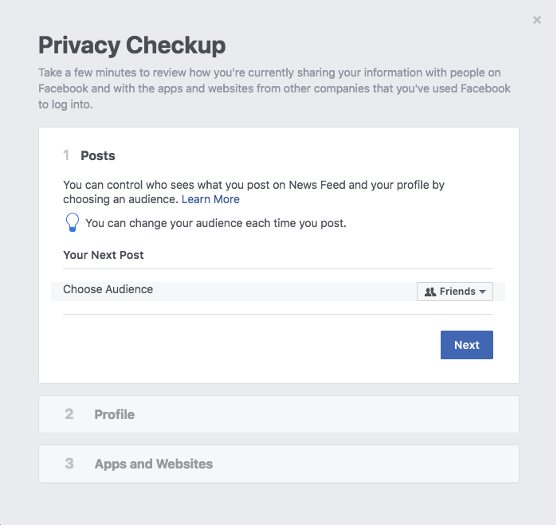
Posts
In this section, we would recommend choosing the Friends setting instead of Public which is usually the default sharing, so you can have the control over your posts and audience who can see what you post.
Profile
Here you can change the privacy settings of your email address, birthday and other personal details which you decide if you want to share with your friends or to keep them private by choosing the “Only me” option.
Apps
This part shows you each app linked to your account and what sharing permission it has. We recommend deleting the apps you’re not using anymore and setting the sharing permissions of the remaining ones to “Only me”.
Step 2
Advanced privacy settings
In this section you can check what content is being shared by your profile and with whom.
Click the drop-down arrow in the top right of your Facebook page, click “Settings,” and then choose “Privacy” from the left navigation column.
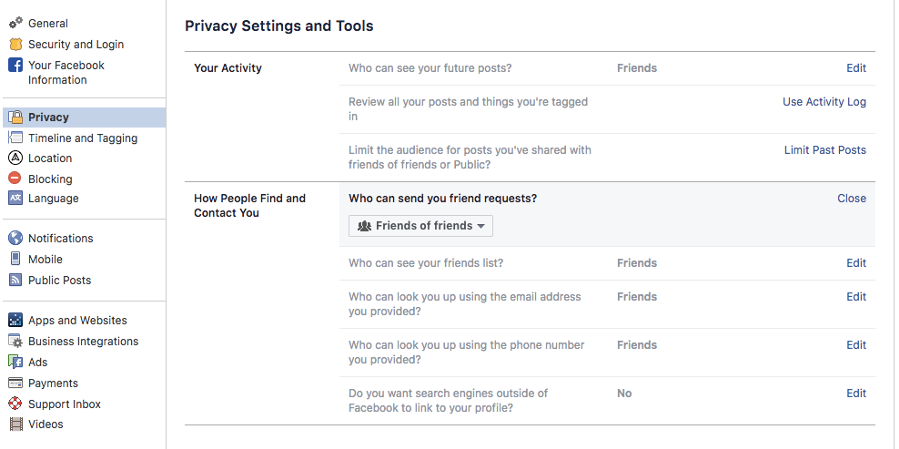
Your activity
In this section you can choose who can see your future posts. We would recommend selecting Friends as your default sharing option, otherwise, if it’s Public, then everything you post is shared with everyone.
The last feature available in the same section is to Limit the audience for old posts on your timeline and by using this, all the audience for the shared content from your timeline will be changed from “Public” or “Friends of Friends” to “Friends”.
How People Find and Contact You
Further on, you can choose who can see your friends list and who can search for your profile by using your email address and phone number, which would be advised to be restricted “Only me”.
With regards to your profile appearing among name-based queries’ results on search engines, by selecting “No” in the dedicated section of this page, your profile could be found only through Facebook search
Step 3
Timeline and Tagging Settings
This section allows you to work on some other privacy settings, i.e, who can post on your timeline, timeline visibility, tagging and review.
Click on the down arrow in the far upper right corner to reveal a drop-down menu and select “Settings”, and then “Timeline and Tagging”.

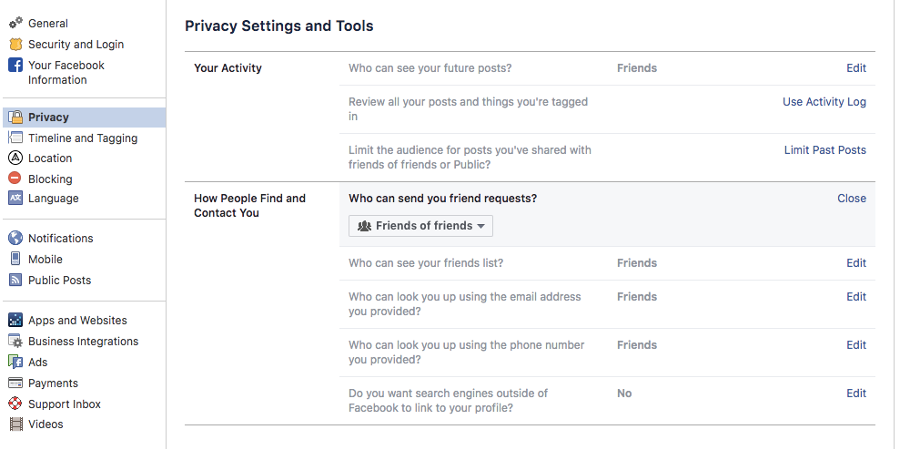
We suggest making your account private
When you join Instagram, anyone can view your profile, photos, posts and comments because your account is set to public by default. For a higher level of privacy, we would recommend switching your account to private to allow only your approved followers to see your posts.
Step 1
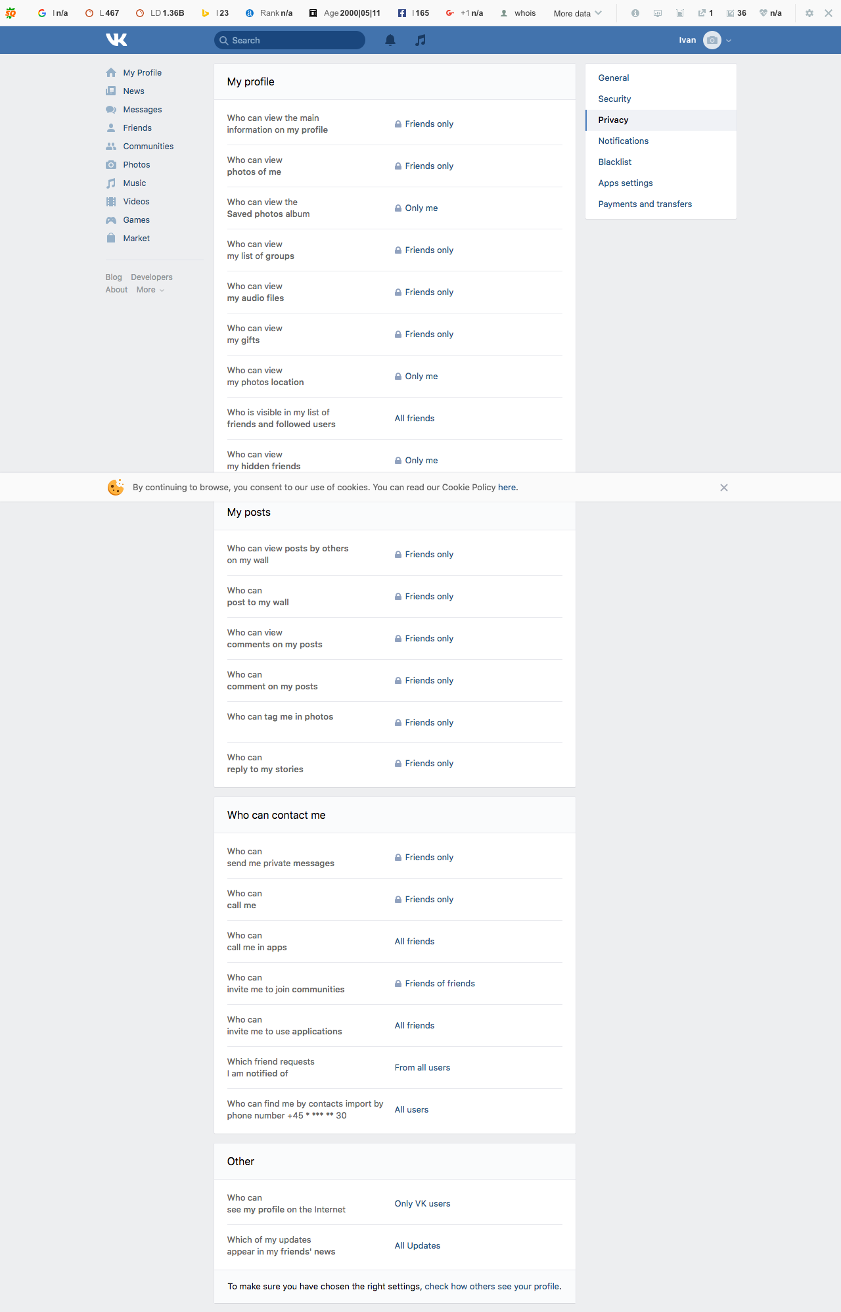
Click the drop-down arrow in the top right of your VK page, click “Settings,” and then choose “Privacy” from the right column: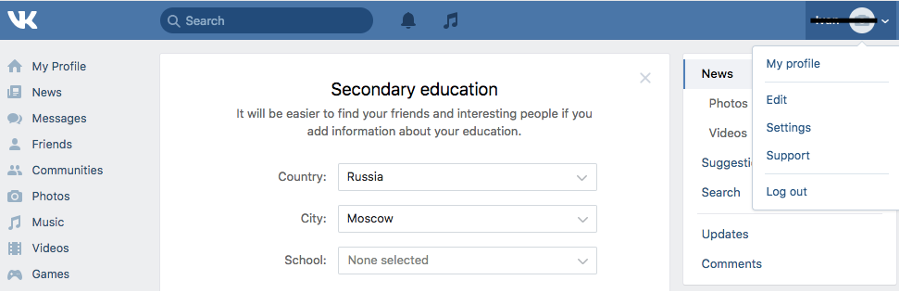
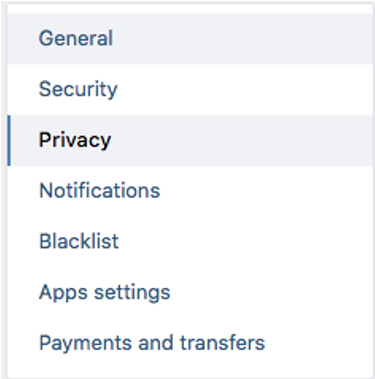
Step 2
Adjust your profile privacy settings
Here you are allowed to change the privacy settings of almost any information that is available on your VK page such as basic information about you, your photos, groups, audio files, gifts, posts, contacts and many others. We would recommend choosing Friends or Only me as the default sharing for most of the settings from “My profile”, “My posts” and “Who can contact me” section and Only VK users for “Who can see my profile on the internet” from the “Other” section.
Interested in a Digital Footprint Report?
What are you waiting for? Contact us for a digital footprint report. The report will include high, medium and low risk cases together with a recommendation on how to prevent and/or remove the unwanted content, and a recommendation on services going forward.
Additional Information
Thomsen Trampedach has assisted more than a dozen brands and regions applying for their own new gTLD. We can help you too.
Thomsen Trampedach can suggest and register domain names across all top-level domains.
Thomsen Trampedach can register user names across social media sites and important local sites.
Offline Actions
Together with our local partners, we can help you with arbitration procedures across all TLDs (UDRP, CNDRP etc.)